If your phone is stolen, a determined thief could access your messages, banking apps, photos, emails and business platforms.
The good news? A few simple settings can make your device almost useless to anyone but you. We’ve pulled together five powerful steps you can take today to keep your data safe and your mind at ease.
Five ways everyone can improve the security of their phone
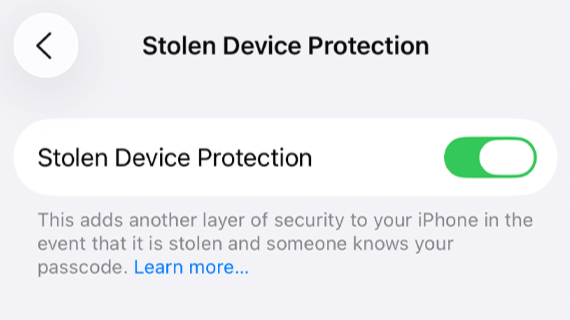
1. Turn on theft protection
iPhone Go to Settings > Face ID & Passcode > Stolen Device Protection. This stops key actions like changing passwords or turning off “Find My” without biometric confirmation — even if the thief knows your passcode.
Android Enable Theft Detection Lock (in Settings > Security) to automatically lock the phone if suspicious movement is detected after theft.
2. Disable access to the control centre, live activities and accessories from the lock screen
By default, some iPhone features can be accessed without unlocking, which could help a thief.
Go to Settings > Face ID & Passcode, then scroll down and switch off:
Control Centre stops thieves from enabling Airplane Mode, which would otherwise disable tracking tools like Find My iPhone.
Live Activities hides real-time notifications (like delivery updates or calendar events) that could leak personal information.
Wallet prevents access to Apple Pay and stored payment cards from the lock screen, stopping thieves from attempting contactless payments.
Accessories blocks new devices (like a malicious USB or Bluetooth accessory) from connecting without authentication.
This reduces the chance of a thief tampering with your device before you can act.
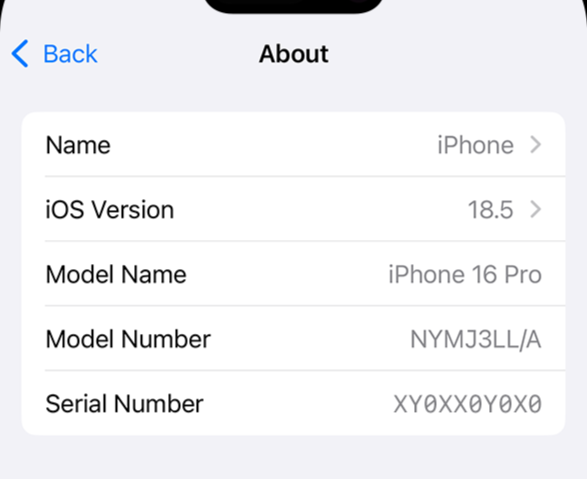
3. Make a note of your IMEI number
Your IMEI is a unique 15-digit number that identifies your device. If your phone is stolen, police and your network provider can use it to block the device and improve your chances of recovery.
Find it by dialling *#06# or in Settings > General > About (on iPhone) or Settings > About phone (on Android).
Email it to yourself or save it on a different device so you can access your IMEI number if your phone is lost or stolen.
4. Hide your critical apps in a hidden folder
Make it harder for thieves to find and access your most sensitive apps.
iPhone
Use the App Library - Long press on the banking app > tap Remove App > choose Remove from Home Screen. This hides it from the main screen but keeps it searchable.
Hide apps in a folder - Drag your banking apps into a folder with less obvious apps (like “Utilities” or “Tools”) and move that folder to the last page of your Home Screen.
Hide entire Home Screen pages - If you prefer, you can still create a new page with your banking apps and untick it (long press on the Home Screen > tap the dots > untick the page) to remove it completely from view.
How to find them again:
Swipe down on the Home Screen and use Spotlight Search to type the app name.
Swipe to the far right to open the App Library — your hidden apps will still be there.
If you hid a whole page, go back to the Home Screen editor (tap and hold > dots) and re-enable the page.
Face ID
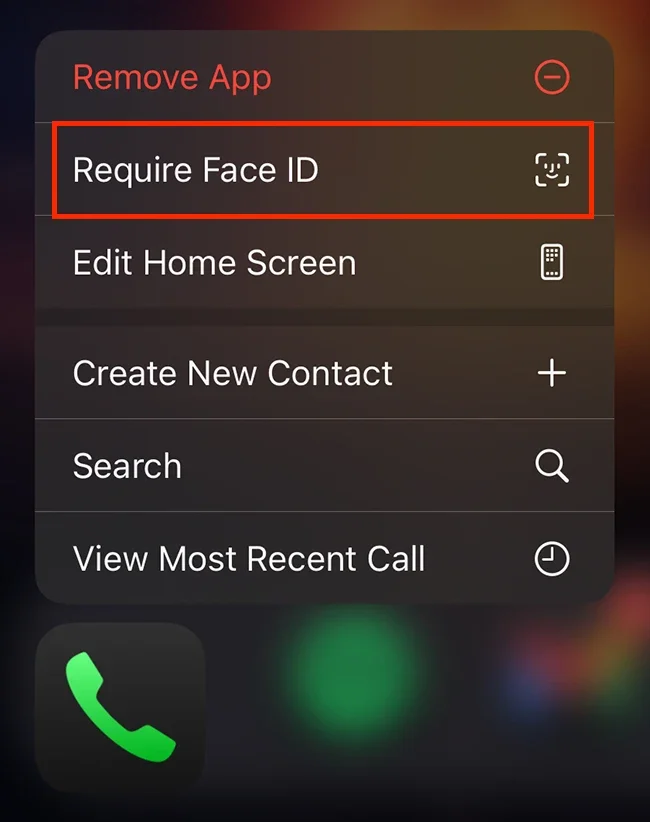
Many apps allow you to use Face ID to open them — meaning even if a thief finds the app, they still can’t get in.
Select the app you want to protect from your iPhone Home Screen.
Press and hold the app icon until a quick action menu appears.
If the app supports biometric security, you’ll see an option like “Require Face ID” or “Enable Face ID”.
Tap it to enable biometric authentication instantly.
Once enabled, the app will require your face or fingerprint every time it’s opened, even if the phone itself is already unlocked.
Android
Use Secure Folder (Samsung) - Go to Settings > Security > Secure Folder and move your banking apps there. They’ll be hidden behind a PIN, pattern, or biometric lock.
Hide apps from the Home Screen - Long-press an app > Hide or Remove from Home Screen to make it less visible.
Use app-lock features - Many Android versions allow you to lock individual apps behind fingerprint or face unlock in Settings > Security > App Lock.
How to find them again:
Use the search bar or open the App Drawer.
Access Secure Folder directly (Samsung) or re-enable hidden apps from the launcher’s settings.
5. Lock your iPhone from your Apple Watch
Please note there are variations to these steps between iOS versions. If you need some assistance please feel free to contact our support team.
Step 1: Create a “Lock Phone” Focus mode on iPhone
Open the Settings app on your iPhone.
Tap Focus > + (plus) in the top-right corner.
Select Custom and name it something like “Lock Phone”.
Choose an icon and colour (this doesn’t matter functionally — it’s just for identification).
You don’t need to configure any notifications or app filters for this Focus. Tap Done.
Step 2: Create a Shortcut automation to lock your iPhone
Now we’ll make your iPhone automatically lock itself whenever this Focus is turned on.
Open the Shortcuts app.
Go to the Automation tab and tap + > Create Personal Automation.
Scroll down and select Focus.
Choose the “Lock Phone” Focus you just created.
Make sure it’s set to trigger When Turned On, then tap Next.
Tap Add Action > Scripting > Lock Screen. (in iOS26 you can find Actions within “Create new shortcut” - In the search bar at the bottom type Lock Screen, you’ll see it under Scripting / Device / Lock Screen)
Tap Next again and turn Ask Before Running to Off (confirm by tapping Don’t Ask).
Now, every time you enable the “Lock Phone” Focus, your iPhone will lock itself immediately.
Step 3: Trigger the lock from your Apple Watch
Focus modes sync automatically between your iPhone and Apple Watch, you can activate the lock remotely from your wrist:
Swipe up (or press the Side Button) on your Apple Watch to open Control Centre.
Tap the Focus icon (crescent moon).
Select the “Lock Phone” Focus you created.
Within a second or two, your iPhone will lock itself instantly, even if it’s still unlocked and in someone else’s hands. This means:
They’ll need your Face ID or passcode to continue using the phone.
They won’t be able to turn off Find My iPhone or access your data.
It buys you valuable time to track, mark as lost, or remotely erase the device.
Roadmap can help businesses improve the security of their mobile devices.
Our certified, and experienced team can improve the security of your mobile devices to help reduce your risk of data loss, or unauthorised access to systems or applications due to theft or a cyber security event. This can be achieved by implementing:
1. Mobile Device Management
Protect devices, settings, data and apps
2. Conditional Access Policies
Enforce identity and access controls
3. Endpoint Threat Detection
Protection from malware, phishing, network attacks
4. Zero Trust Access
App control, network access
5. User Awareness
Training and awareness